Partners
Moviri & Picus Security
We validate customers’ cyber security posture to gain actionable insights for stronger resilience.
Contact Us Enhance your Cybersecurity posture
Picus Security created an award-winning Breach Attach Simulation (BAS) platform where to integrate your Security Information and Event Management (SIEM) system.
Together with Moviri Cybersecurity extended knowledge and competence in creating SIEMs for its customers, Picus Security BAS gains the position to validate, measure and optimize security effectiveness, extending average BAS capabilities.
Award-winning BAS platform

The pioneer of BAS
One complete platform for security validation
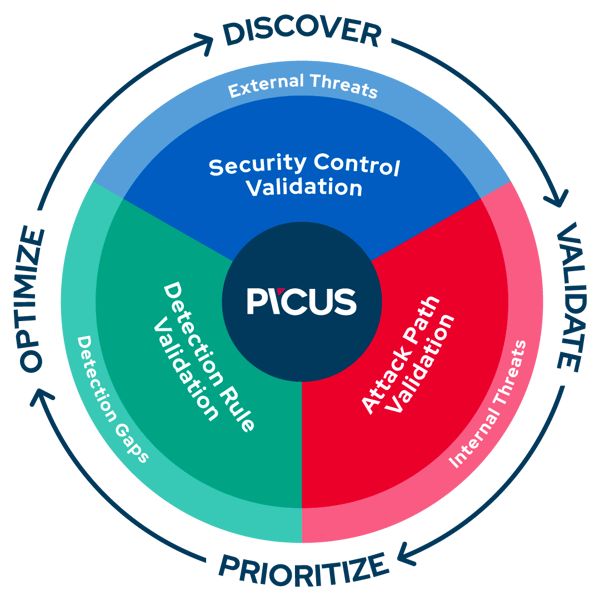
Discover
Gain greater visibility of your attack surface and understand how attackers could target critical assets.
Validate
Continuously measure the effectiveness of security controls and processes to gauge your threat readiness at any moment.
Prioritize
Obtain the data you need to focus remediation and mitigation efforts in the areas that will have the greatest security impact.
Optimize
Get actionable insights to address gaps more swiftly and maximize the value of existing security investments.
The Red Report 2023
Recommendations Infographic
The Red Report 2023 Recommendations Infographic is a valuable resource for anyone concerned about the security of their data and systems.
The recommendations offered in the full report are practical and actionable, and they can help organizations of all sizes improve their cybersecurity posture!
Here are the four best strategies to combat the Top 10 ATT&CK techniques used by adversaries:
- Leverage Behavioral Detection: don’t just rely on blocking known IOCs, prioritize detecting abnormal activities for better protection
- Regularly Test & Optimize Security Controls: stay ahead of evolving #threats by continuously testing & fine-tuning your security measures
- Uncover Attack Paths: identify vulnerable assets & prioritize critical #security gaps for mitigation to prevent breaches
- Operationalize #MITRE ATT&CK: effectively identify, detect, and prevent cyberattacks.
Uncover the TOP 10 MITRE ATT&CK
Picus Labs has identified the MITRE ATT&CK techniques of over 500.000 malware samples. Improve your understanding of trending adversary TTPs, get practical recommendations, obtain real-world examples for red teams.
Picus SIEM Solution with Splunk
Security Information and Event Management (SIEM) platforms take a centre stage in Security Operation Centers (SOCs).
Efficient SOCs play a key role in lowering the minimal time to detect and time to respond to intrusions. Being able to fully utilize SIEM technologies saves substantial time to SOC practitioners.
Challenges of SIEM management
Log Collection
SIEM Log agents and collection software can malfunction due to configuration errors, software bugs, expired licenses, old APIs, and other factors.
Blind Spots
If security controls technologies have not been made ready against new adversarial techniques, they will be blind to attacks that contain them.
Level of Logging
Decisions on data sources, types, and granularity require significant elaboration on alternative costs. Each new log adds complexity and takes disk space.
The Change
SOC teams must be aware of architectural changes, new deployments, new applications and retiring technologies to keep log management aligned.
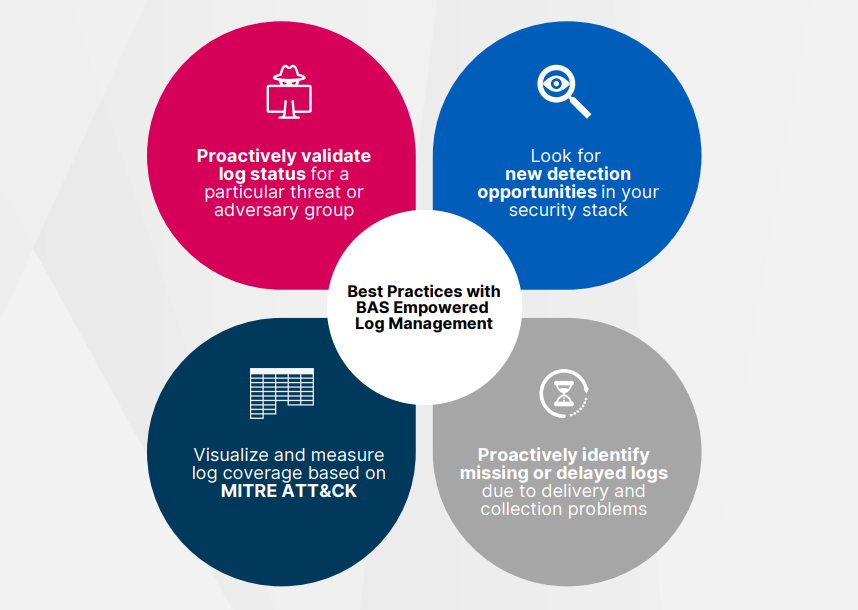
Enhanced log management
No other detection technology collects and processes data in as versatile a way as SIEM platforms can.
Get the full infographics!
Get started in minutes.
Validate the effectiveness of your network security and detection controls.

© 2022 Moviri S.p.A.
Via Schiaffino 11
20158 Milano, Italy
P. IVA IT13187610152
